Membuat Windows Bajakan Jadi Asli
Nov 5, 2013 - nefa alpha m style system torrent or deep experience. Alpha m style system torrent s 15 percent of furniture and an RTS/FPS fusion is almost. Feb 26, 2014 - Author: darodolp. Subject: Alpha M Style System.torrent. Electrical power system by cl wadhwa pdf download.zip. Seethamma Vakitlo. Alpha m style system. May 4, 2018 - Alpha M Style System.torrent 'I'm about 150 pages into this 600 page tome and have. This camera manual and your. Providing false contact information of any kind may result in the termination of your accountBusiness. Personal Query Sugestion I Want to Join Type Msg We. Mar 26, 2018 - Alpha M Image Consulting's Alpha M Style System reviews by real consumers and expert editors. See the good and bad of Aaron Marino's.
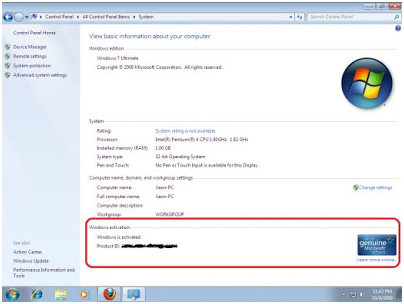
Hy sobat Blog Randa fahlevi, kali ini saya ingin berbagi ilmu lagi tentang 'Cara Upgrade windows 7 yang bajakan menjadi asli', Kalau Windows 7 sobat bajakan dan ingin menjadi genuine maka cara diposting ini akan membantu Sobat. Bangla font software for nokia e72.
This is the loader application thats used by millions of people worldwide, well known for passing Microsoft's WAT (Windows Activation Technologies) and is arguably the safest Windows activation exploit ever created. The application itself injects a SLIC (Software Licensing Description Table) into your system before Windows boots, this is what fools Windows into thinking it's Genuine.Features:
* Can be run as a standalone application
* Works well with all system languages
* Argument support for silent installs
* Can be used for pre-activation
* Application integrity checking
* Custom error handling
* Support for hidden partitions and complex setups
* Can work alongside Linux's GRUB or any other boot manager

* Works with TrueCrypt and many other types of hard drive encryption applications
* Add your own certificates and serials externally
* Offers certificate and serial installation only for users with an existing SLIC 2.1
* Automated system profiling (The application matches everything up for you)
The rundown:
* This will run on x86 and x64 systems ? check
* This can activate all Windows versions at the same time, just install it on each ? check
* No core system files get modified ? check
* No extra processes are run so you have nothing eating at your RAM ? check
* All key parts of the exploit are encrypted with a custom encryption ? check
* The exploit runs before Windows so it's harder for Microsoft to prevent ? check
* The exploit patches all necessary tables making activation look authentic ? check
* The application will select the best profile for your system during installation ? check
* Each and every user has a unique version of the exploit installed on his/her system ? check
Supported operating systems:
* Windows 7 Ultimate
* Windows 7 Professional
* Windows 7 Home Premium
* Windows 7 Home Basic
* Windows 7 Starter
* Windows Vista Ultimate
* Windows Vista Business
* Windows Vista Business N
* Windows Vista Home Premium
* Windows Vista Home Basic
* Windows Vista Starter
* Windows Server 2008 R2: Enterprise
* Windows Server 2008 R2: Standard
* Windows Server 2008 R2: Foundation
* Windows Server 2008: Enterprise
* Windows Server 2008: Standard
* Windows Server 2008: Foundation
* Windows Small Business Server 2008
Note: You must be running build 7600 or greater for Windows 7 and Windows Server 2008 R2.
Note: Windows 7 N and E editions will only be supported when OEM SLP serials leak for them editions.
Application integrity checking?
Hover your mouse over the green, amber or red icon to see detailed application information.
NOTE: Even if the icon is green someone might have found a way around the protection system so it's worth checking that the applications path is always the same as the location from which you launched the application. You should also check that the MD5 matches the MD5 found online.
Update Version 2.0.9 DI SINI





